| Table of Contents |
|---|
Introduction
...
Configure SNMPTRAPS to scale up to 300 traps per second. The purpose of this article is to show how to configure the SNMPTRAPD to pull data from the devices to rsyslog. Then, the rsyslog collects the logs into a file to be processed by opEvents. Eventually, the opEvents will apply the filters, parsers, and actions to better use the system management, analysis, and troubleshooting based on the events.
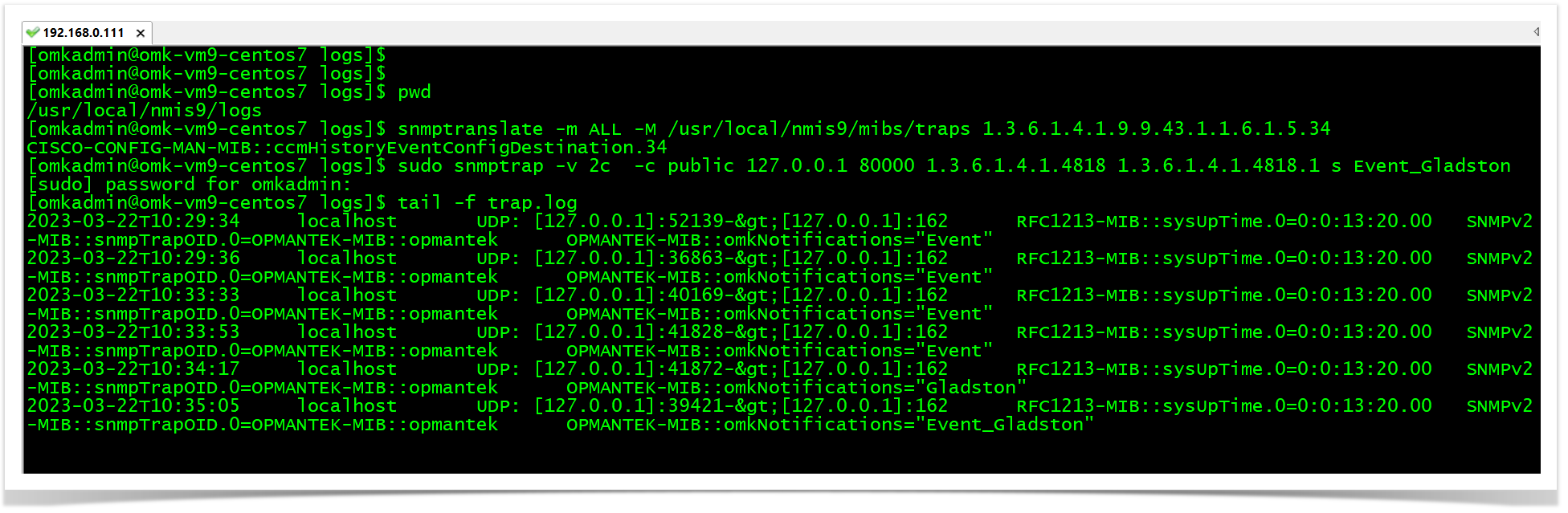
Testing SNMPTRAPS:
snmptranslate -m ALL -M /usr/local/nmis9/mibs/traps 1.3.6.1.4.1.9.9.43.1.1.6.1.5.34
***************************************************************************************************
...
***************************************************************************************************
sudo snmptrap -v 2c -c public 127.0.0.1 80000 1.3.6.1.4.1.4818 1.3.6.1.4.1.4818.1 s Event
...
Step-by-Step How to Configure the SNMPTRAPS to Forward Traps to Sylog
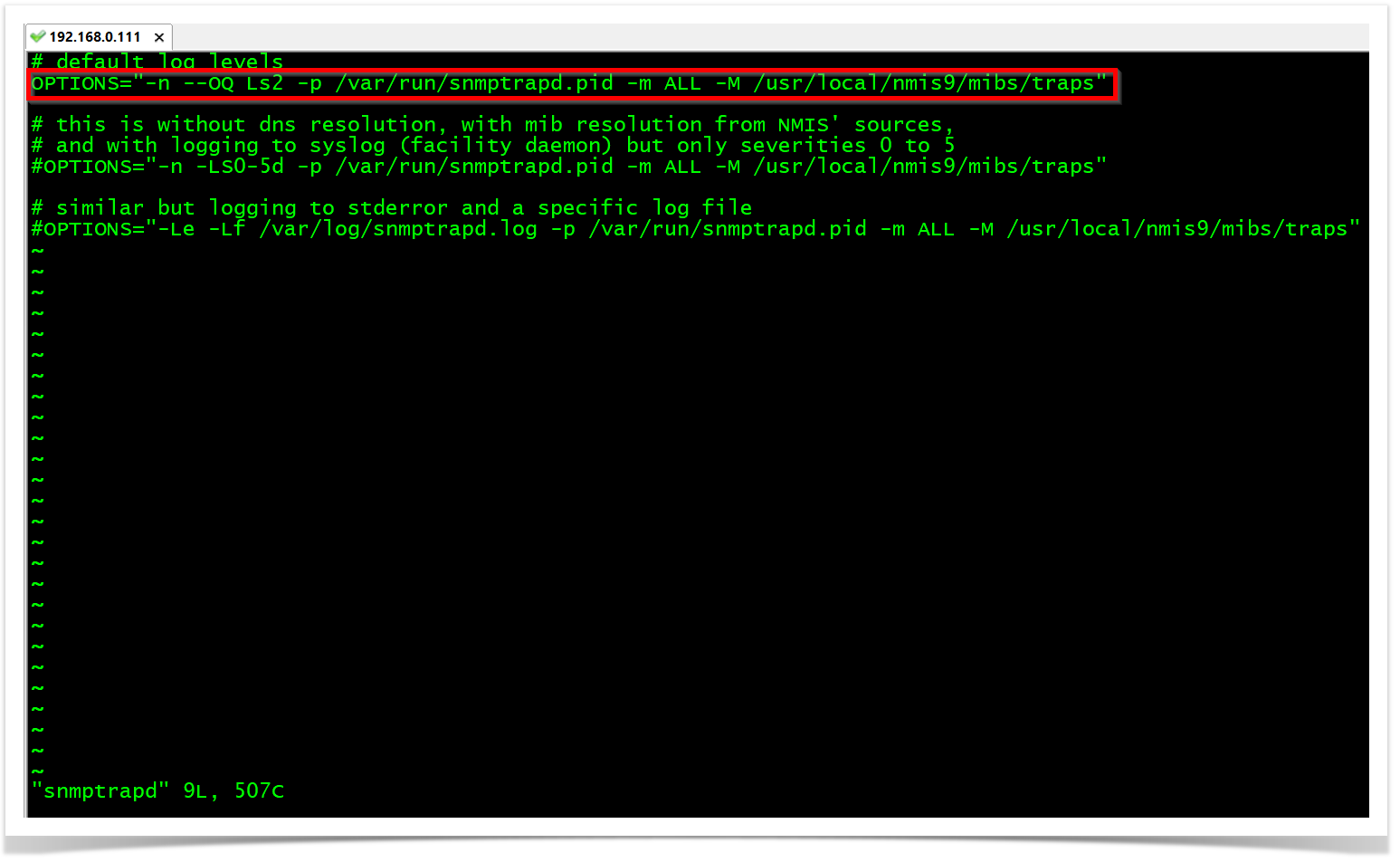
OBSERVATION: The "Ls" option will configure snmptrapd to send logs to syslog. So, "Ls2" specifically configures snmptrapd to send logs from the local2 facility. The facility is a value that indicates which process on the device generated the message.
STEP 1
RHEL/CENTOS Linux
cd /etc/sysconfig/
vim snmptrapd
...
OPTIONS="-n --OQ Ls2 -p /var/run/snmptrapd.pid -m ALL -M /usr/local/nmis9/mibs/traps"
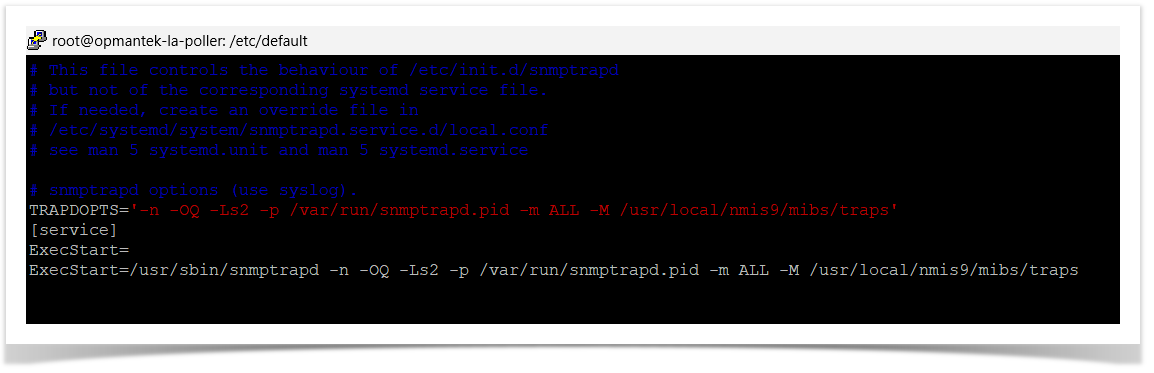
Debian/Ubuntu Linux
cd /etc/default/
vim snmptrapd
...
TRAPDOPTS='-n -OQ -Ls2 -p /var/run/snmptrapd.pid -m ALL -M /usr/local/nmis9/mibs/traps'
[Service]
ExecStart=
ExecStart=/usr/sbin/snmptrapd -n -OQ -Ls2 -p /var/run/snmptrapd.pid -m ALL -M /usr/local/nmis9/mibs/traps
STEP 2
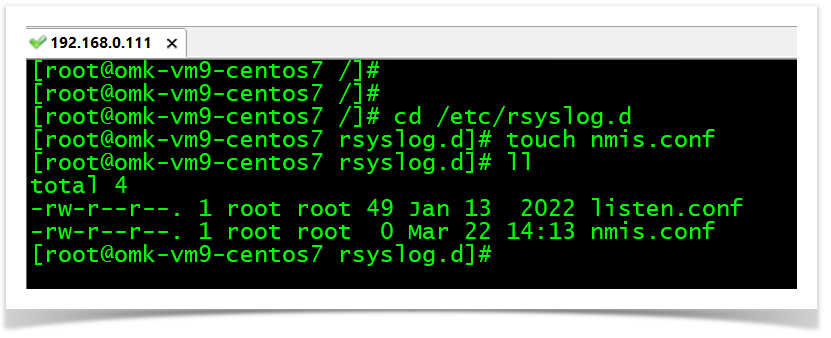
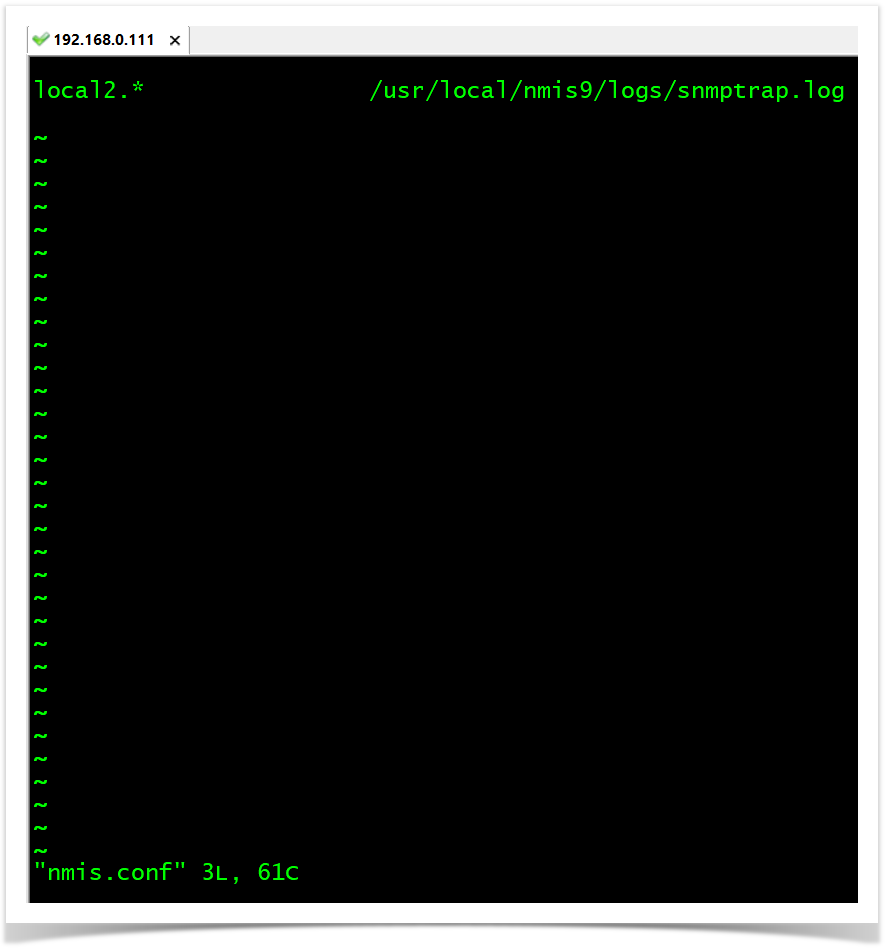
We need to configure the traps to go to a specific log file for opEvents to process them. In this case, all messages that come from facility local2 will be collected into /usr/local/nmis9/logs/snmptrap.log file.
cd /etc/rsyslog.d
touch nmis.conf
vim nmis.conf
local2.* /usr/local/nmis9/logs/snmptrap.log
cd /etc
vim rsyslog.conf
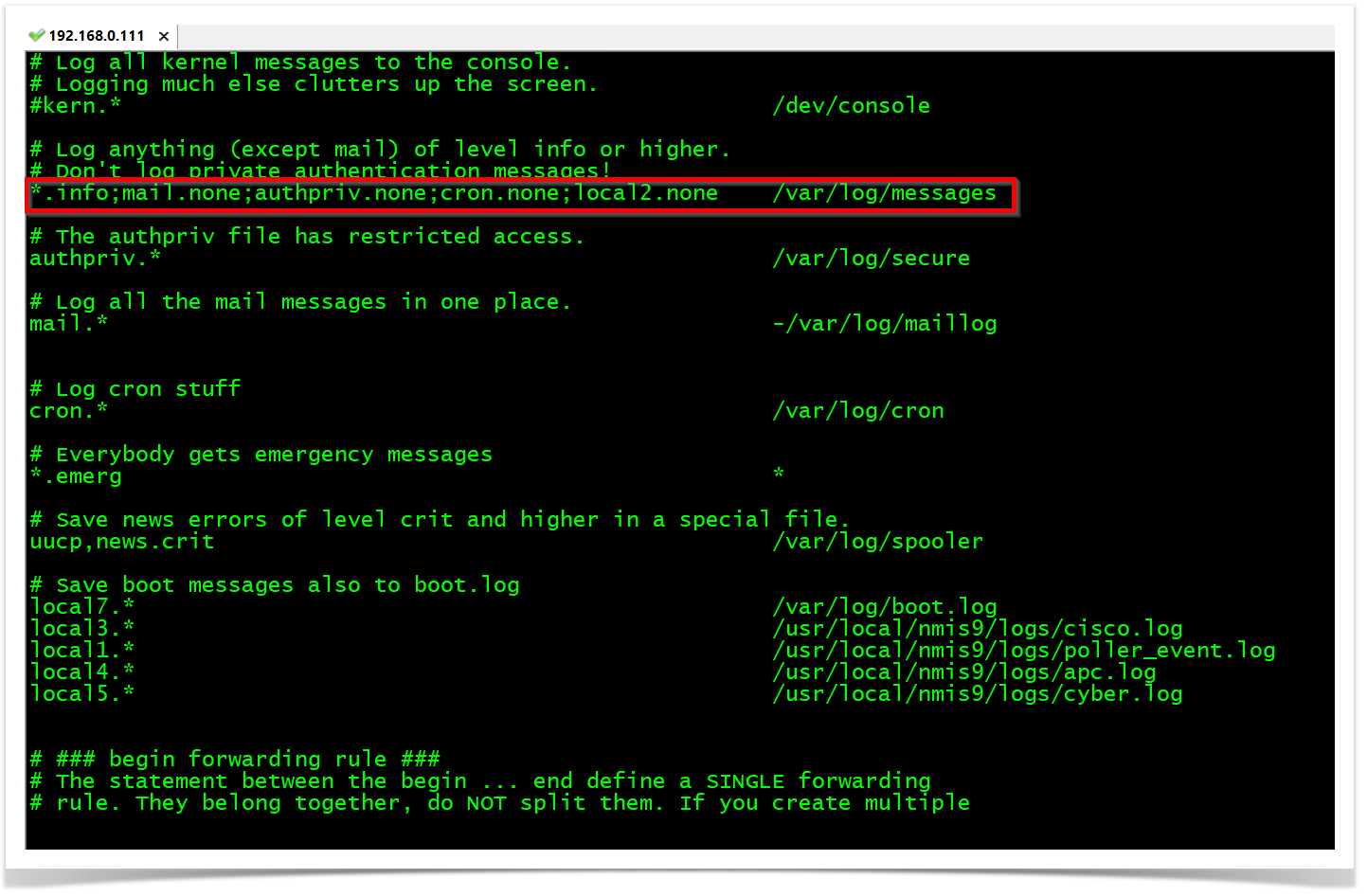
*.info;mail.none;authpriv.none;cron.none;local2.none /var/log/messages
STEP 3
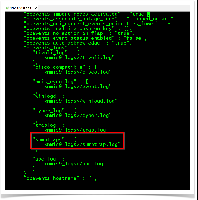
Now, we need to inform OpEvents where the snmptrap comes from. So, we do so, informing the path where the snmptrap.log is on the /usr/local/omk/conf/opCommon.json.
***************************************************************************************************************************************************
Be careful with this opCommon.json file. It is a Perl hash, so any syntax error will render the OMK Server to stop working properly.
We recommend always creating a backup of this file before any changes.
***************************************************************************************************************************************************
cd /usr/local/omk/conf/
vim opCommon.json
STEP 4
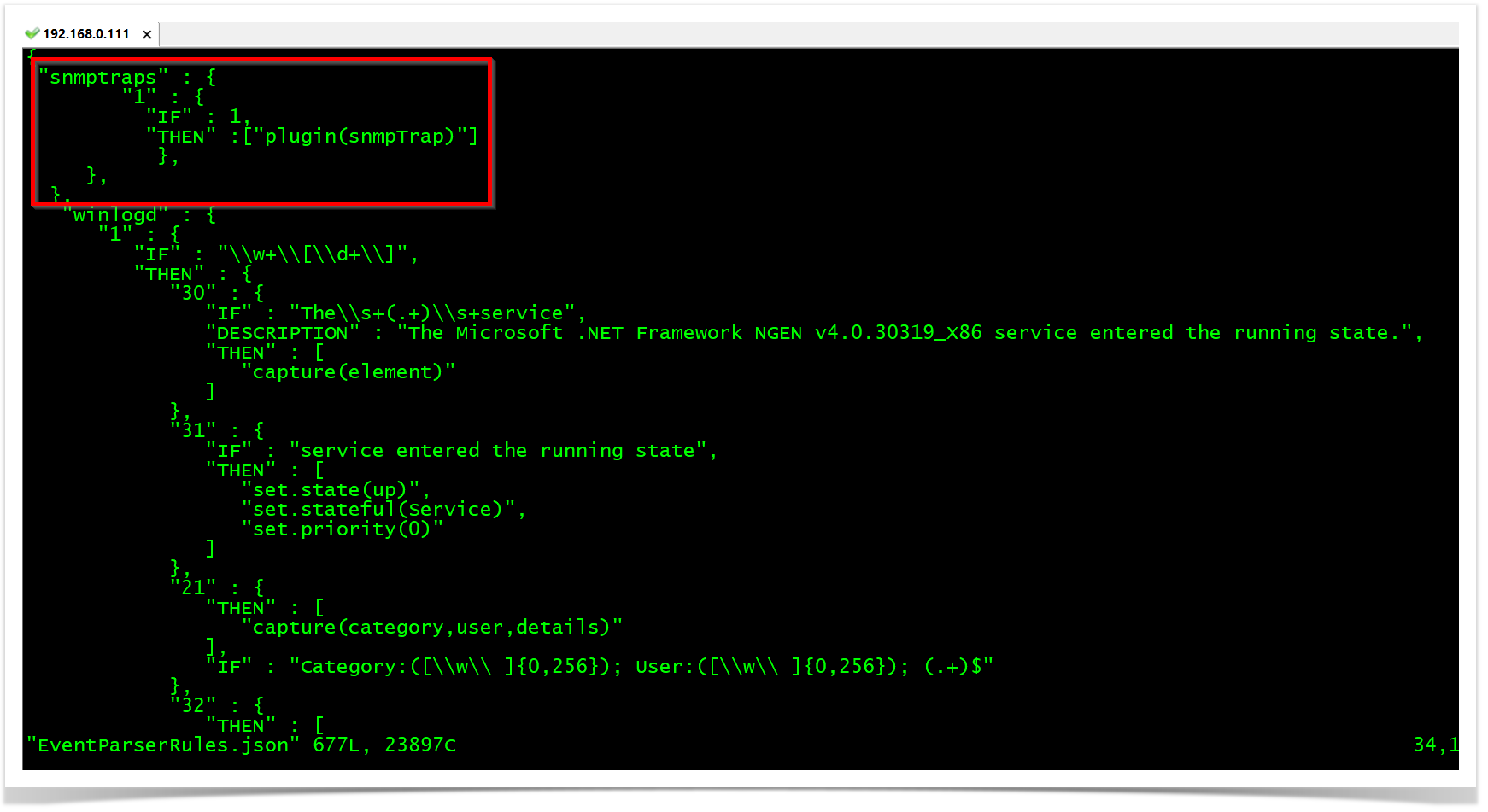
The parser is made on the EventPaserRules.json file. In this case, we are sending to an opEvents plugin to do the syntax translation.
cd /usr/local/omk/conf/
vim EventParserRules.json
STEP 5
cd In step 4, you added the snmptraps plugin parser rules in the EventParserRules.json file. Now, we need to copy the snmpTrap.pm file on the /usr/local/omk/conf/parser_plugins/
vim snmpTrap.pm
package snmpTrap;
our $VERSION="0.0.1";
use strict;
# arguments: the line (currently being parsed),
# and reference to the live event properties
# returns: (status-or-error)
#
# zero or undef: parsing for this event is aborted,
# and no event is created.
# 1: indicates success, event is created and changed event
# properties are incorporated.
# any other value: treated as error message, changed event
# properties are NOT incorporated but event parsing continues.
sub parse_enrich
{
my ($line, $event) = @_;
my $ditch = 0;
$event->{"details"} = $line;
my @halves = split("#012", $line);
my @OIDs = split('#011', $halves[1]);
#my @OIDs = split('#011', $halves[1]);
my ($ipaddress) = $halves[0] =~ /UDP:\s+\[(\d+\.\d+\.\d+\.\d+)\]/;
my ($date) = $halves[0] =~ /(\d{4}-\d\d-\d\d \d\d:\d\d:\d\d)/;
$event->{"ipaddress"} = $ipaddress;
$event->{"host"} = $ipaddress;
$event->{"date"} = $date;
foreach my $i (@OIDs) {
my @parseOID = split('=', $i);
## OID
my $varname = $parseOID[0];
$varname =~ s/\s+$//;
my @oidValue = split(/\s+/, $parseOID[1],3);
## OID value
my $rest = $oidValue[2];
$rest =~ s/\s+$//;
# trapoid: sets the event name
if ($varname eq "SNMPv2-MIB::snmpTrapOID.0")
{
$event->{event} = $rest;
# no next, keep the trapoid as it came in - fixme or copy as 'trap' and next?
}
# ...other /parsing/ rules go here, may end with next; if varname => rest is
# not desirable in the event
if ( $event->{event} eq "IF-MIB::linkDown" ) {
$event->{event} = "Interface Down";
$event->{stateful} = "Interface";
$event->{state} = "down";
$event->{priority} = 3;
}
elsif ( $event->{event} eq "IF-MIB::linkUp" ) {
$event->{event} = "Interface Up";
$event->{stateful} = "Interface";
$event->{state} = "up";
$event->{priority} = 2;
}
elsif ($varname =~ /IF-MIB::ifIndex\.\d+/ )
{
$event->{element} = $rest;
}
elsif ($varname =~ /IF-MIB::ifDescr\.\d+/ )
{
$event->{element} = $rest;
}
elsif ($varname eq "OSPF-MIB::ospfNbrState")
{
$event->{stateful} = "OSPF Neighbor";
if ( $rest eq "down" ) {
$event->{event} = "OSPF Neighbor Down";
$event->{state} = "down";
$event->{priority} = 4;
}
elsif ( $rest eq "up" ) {
$event->{event} = "OSPF Neighbor Up";
$event->{state} = "up";
$event->{priority} = 2;
}
}
elsif ($varname eq "OSPF-MIB::ospfNbrIpAddr" )
{
$event->{element} = $rest;
}
elsif ( $event->{event} =~ /BGP4-MIB::bgpBackwardTransition|BGP4-MIB::bgpTraps.0.2/ ) {
$event->{event} = "BGP Neighbor Down";
$event->{stateful} = "BGP Neighbor";
$event->{state} = "down";
$event->{priority} = 4;
}
elsif ( $event->{event} =~ /BGP4-MIB::bgpEstablished|BGP4-MIB::bgpTraps.0.1/ ) {
$event->{event} = "BGP Neighbor Up";
$event->{stateful} = "BGP Neighbor";
$event->{state} = "up";
$event->{priority} = 2;
}
elsif ($varname =~ /BGP4-MIB::bgpPeerState\.(\d+\.\d+\.\d+\.\d+)/ )
{
$event->{element} = $1;
}
# nobody shortcircuited us? then save the right hand side under whatever varname is now
$event->{$varname} = $rest;
}
if ( $event->{details} =~ /CISCO-CONFIG-MAN-MIB::ciscoConfigManEvent .+ ccmHistoryEventConfigDestination\.\d+=running/ )
{
$event->{event} = "Node Configuration Change";
}
# return 1; # happy, go on, use my changes
# return 0; # ignore this event
# return "i have a problem"; # error, do not use my changes
if ( $ditch == '1' ) {
return 0;
}
else {
return 1;
}
}
directory. This file is the OpEvents parser plugin. The plugin is not always needed. The traps can be collected using the event handler nmis traplog. However, the plugin can parser more complex SNMP traps.
cd /usr/local/omk/conf/parser_plugins/
vim snmpTrap.pm
***************************************************************************************************************************************************
snmpTrap.pm file Download here: snmpTrap.pm
***************************************************************************************************************************************************
STEP 6
Restart the daemons associated.
systemctl restart rsyslog
systemctl restart opeventsd
systemctl restart snmptrapd
1;