| Table of Contents | ||||
|---|---|---|---|---|
|
The audit function of Open-AudIT is designed to work "out of the box" as much as possible with the default settings of target devices. Below are the requirements for the audit to work and some hints for items to configure when things are not working as planned.
...
| Code Block |
|---|
\HKEY_USERS\.DEFAULT\Software\Microsoft\Windows Script\Settings |
DCOM
Run the DCOM utility and verify (or set) the below attributes. Start -> Run, Enter DCOMCNFG and press OK. This will open the DCOMCNFG window.
...
The above changes will require a reboot to take effect.
UAC
If you are getting an Access Denied scan error it might be UAC blocking inbound requests on the remote device. If the remote computer you are trying to query is in a workgroup (or not joined to a domain), UAC prevents remote queries by default, even if the account being used is in the Administrators group. Completely disabling UAC on the remote device allows you to get around this, but it is preferable to disable the subcomponent of UAC instead. You can do this by adding or editing this registry key on the remote device you are scanning and setting its value to 1:
...
The above change will require a reboot to take effect.
Local Security Policies
Run one of the following three Microsoft Management Console (MMC) snap-ins:
...
The above changes will require a reboot to take effect.
Simple File Sharing (XP)
Windows XP Professional computers in a workgroup environment will need simple file sharing disabled. You can make this change through the registry by setting the following key to a value of 0.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\ForceGuest
If this key does not exist, you can add it using a command prompt by:
| Code Block | ||
|---|---|---|
| ||
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa /v ForceGuest /t REG_DWORD /d 0 /f |
You can also do this through settings by performing the following steps:
...
Uncheck the Use simple file sharing (Recommended) to disable the option and click the OK button.
SSPI means Security Support Provider Interface and is the interface used by VBscript / WMI to validate the user.
- If ForceGuest is enabled (set to 1), SSPI will always try to log on using the Guest account.
- If the Guest account is enabled, an SSPI logon will succeed as Guest for any user credentials.
- If the Guest account is disabled, an SSPI logon will fail even for valid credentials.
- If ForceGuest is disabled (set to 0), SSPI will log on as the specified user.
...
The above changes will require a reboot to take effect.
WMI
Windows WMI (Windows Management Interface) is used by the audit script for most of it's information retrieval. WMI can (at times) become corrupted. Microsoft have released a tool to enable you to check for this corruption.
...
For Windows Core servers, ensure you allow the firewall connections as per - http://blogs.technet.com/b/brad_rutkowski/archive/2007/10/22/unable-to-remotely-manage-a-server-core-machine-mmc-wmi-device-manager.aspx
AntiVirus
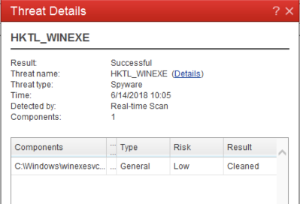
Some antivirus programs have been known to disable DCOM and remote WMI. You might check the settings of your antivirus program and disable them for testing. We recently had a report of Trend AV specifically blocking calls to winexesvc when auditing Windows computers.
Windows Firewall
To enable remote PCs to be audited, either the local (on the target machines) firewall (likely the Windows Firewall) must be disabled or access allowed for the WMI service.
For Windows Vista, 7, 8, 2008 and 2012, enter the following commands:
| Code Block | ||
|---|---|---|
| ||
netsh firewall set service type=remoteadmin mode=enable netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes netsh advfirewall firewall set rule group="remote administration" new enable=yes netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv4-In)" new enable=yes |
...
NOTE - Running as different users will generate a different list of environment variables.
SSHGuard
If you find your target machine is not correctly being audited, check to make sure SSHGuard has not been triggered. Below you can see the IP 192.168.1.179 has been blocked by SSHGuard (see last line).
| Code Block |
|---|
root@desktop:/# iptables -L -n -v
Chain INPUT (policy ACCEPT 77217 packets, 48M bytes)
pkts bytes target prot opt in out source destination
35M 43G sshguard all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 77202 packets, 48M bytes)
pkts bytes target prot opt in out source destination
Chain sshguard (1 references)
pkts bytes target prot opt in out source destination
77 6368 DROP all -- * * 192.168.1.179 0.0.0.0/0 |
To enable your Open-AudIT server, edit the file /etc/sshguard/whitelist and restart the sshguard service.
| Code Block |
|---|
sudo nano /etc/sshguard/whitelist
sudo service sshguard restart |
ESX
On VMware ESX, Open-AudIT uses SSH as it's primary method of auditing. SNMP is also supported (and detailed below).
...
SNMP v1, v2c and v3 are supported. Read access is required.