...
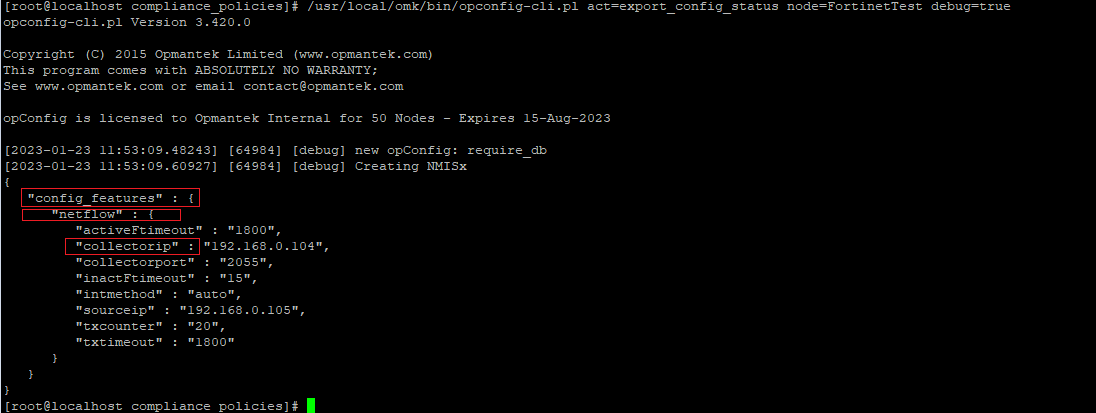
In this example we want to extract the Netflow configuration cofiguration on a Fortigate device. Fortigate command that have the information we need "show full-configuration system netflow"
...
| Code Block |
|---|
# json_xs < opCommon.json |
Note that all matching parsers will be applied for a particular command, in the order they are given in the configuration.
...
| Code Block |
|---|
[root@localhost conf]# /usr/local/omk/bin/opconfig-cli.pl act=export_config_status node=FortinetTest debug=true
opconfig-cli.pl Version 3.420.0
Copyright (C) 2015 Opmantek Limited (www.opmantek.com)
This program comes with ABSOLUTELY NO WARRANTY;
See www.opmantek.com or email contact@opmantek.com
opConfig is licensed to Opmantek Internal for 50 Nodes - Expires 15-Aug-2023
[2023-01-20 17:32:28.57037] [8596] [debug] new opConfig: require_db
[2023-01-20 17:32:28.71590] [8596] [debug] Creating NMISx
{
"config_features" : {
"netflow" : {
"activeFtimeout" : "1800",
"collectorip" : "192.168.0.104",
"collectorport" : "2055",
"inactFtimeout" : "15",
"intmethod" : "auto",
"sourceip" : "192.168.0.105",
"txcounter" : "20",
"txtimeout" : "1800"
}
}
} |
Compliance Policy files.
Compliance policy language is very similar to opEvents language.
Here is a quick overview of the structural rules:
- A policy consists of one hash (or "associative array"). All hash keys (=rule numbers) must be numeric, and the keys control the order of rule evaluation.
Rule numbers do not have to be globally unique, just within the enclosing subpolicy. - Each hash element must describe either one IF/THEN clause or one EACH/BLOCK iteration.
- THEN statements can be either a single string (describing the actions to take) or a nested sub-policy (in the form of a nested hash).
- EACH/BLOCK iterations always require a nested sub-policy.
- IF statements are single strings, made up from structure or variable selector expressions and Perl operators and expressions.
- The available actions for THEN statements are
ok(),exception(),CONTINUE()andLAST(). - EACH statements consist of a variable name (for the iterator variable to be) and a structure selector expression (for the objects to iterate over).
- The policy engine invokes policy rules with a number of pre-defined structure variables, to provide access to the configuration status document, the current node name and a few others
Compliance policy files are installed in the directory /usr/local/omk/conf/compliance_policies and they must have the .json extension.
Step 1. Create compliance policy file.
With the Compliance policy file we are going to evaluate the information that we got on step 4 - Execute the update_config_status and export_config_status commands. We have to create a compliance policy file, navigate to /usr/local/omk/conf/compliance_policies.
| Code Block |
|---|
# cd /usr/local/omk/conf/compliance_policies |
We can copy the cisco_nsa.json policy to create fortigate-netflow.json policy.
| Code Block |
|---|
# cp cisco_nsa.json fortigate-netflow.json |
In our case we want to valided if the Fortigate has the collector IP and collector port configured.
let's edit the fortigate-netflow.json file
| Code Block |
|---|
# vi fortigate-netflow.json |
| Code Block |
|---|
{
"10" : {
"IF" : "not defined(${NODEINFO}.os_info)",
"THEN" : "exception(\"Node has no os_info\",0,node=$NODENAME) AND LAST()",
"Comment" : "If the device does not have a OS information you will get an exception "
},
"20" : {
"IF" : "$NODEINFO.os_info.os eq \"Fortinet\"",
"Comment" : "In our case OS info must macth with Fortinet in order to apply this policy, if you have cisco device you should have IOS or IOS-EX etc",
"Comment" : "This policy will apply only for Fortigate devices",
"THEN" : {
"201" : {
"IF" : "$NODE.config_features.netflow.collectorip eq \"192.168.0.104\"",
"Comment" : "If you want to check if the value on collectorip variable is equal to 192.168.0.104",
"Comment" : "all the variables stored in the inventory are strings, you should evaluate with eq ne etc",
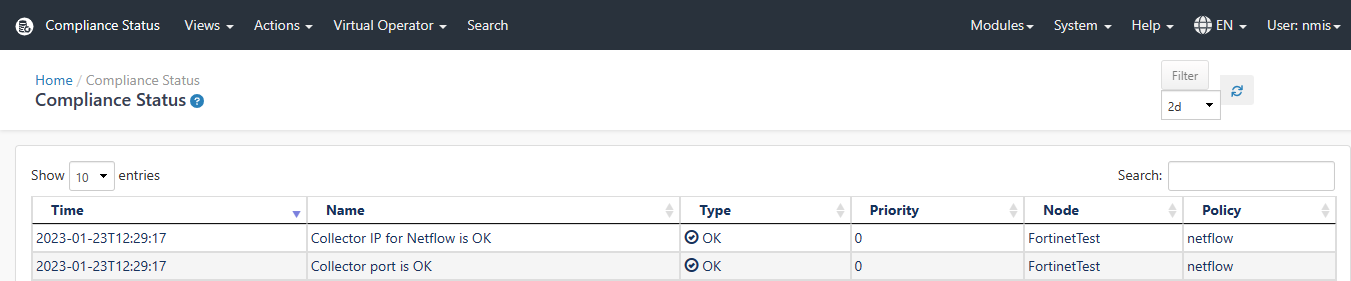
"THEN" : "ok(\"Collector IP for Netflow is OK\",4,node=$NODENAME,config=$NODE.config_features.netflow.collectorip)",
"Comment" : "Output that you will get in opConfig NODE.config_features.netflow.collectorip"
},
"202" : {
"IF" : "$NODE.config_features.netflow.collectorip ne \"192.168.0.104\"",
"THEN" : "exception(\"Collector IP for Netflow is not correct\",3,node=$NODENAME,config=$NODE.config_features.netflow.collectorip)"
},
"203" : {
"IF" : "not($NODE.config_features.netflow.collectorip)",
"Comment" : "if the collectorip is not present on the inventory",
"THEN" : "exception(\"Collector IP for Netflow is not configured\",3,node=$NODENAME,config=$NODE.config_features.netflow.collectorip)"
},
"204" : {
"IF" : "$NODE.config_features.netflow.collectorport eq \"2055\"",
"THEN" : "ok(\"Collector port is OK\",4,node=$NODENAME,config=$NODE.config_features.netflow.collectorport)"
},
"205" : {
"IF" : "$NODE.config_features.netflow.collectorport ne \"2055\"",
"THEN" : "exception(\"Collector port is not correct\",3,node=$NODENAME,config=$NODE.config_features.netflow.collectorport)"
},
"206" : {
"IF" : "not($NODE.config_features.netflow.collectorport)",
"THEN" : "exception(\"Collector port is not configured\",3,node=$NODENAME,config=$NODE.config_features.netflow.collectorport)"
}
}
}
} |
| Warning | ||
|---|---|---|
Compliance policy file does not allow comments. If you copy the code with comments you will get this error when you will try to use the check_compliance command.
|
We can check if the syntaxis is ok using this:
| Code Block |
|---|
# json_xs < fortigate-netflow.json |
We get the variable $NODE.config_features.netflow.collectorip from the inventory output:
Step 2. Execute the import_policy and check_compliance commands.
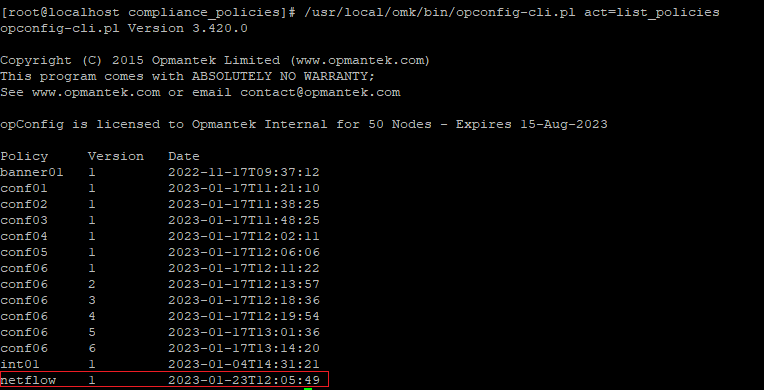
All compliance policies are named and versioned.
To make a policy available to opConfig, it must be imported, we are going to import the fortigate-netflow.json policy like this:
| Code Block |
|---|
# /usr/local/omk/bin/opconfig-cli.pl act=import_policy name="netflow" file=/usr/local/omk/conf/compliance_policies/fortigate-netflow.json
|
List the compliance policies
| Code Block |
|---|
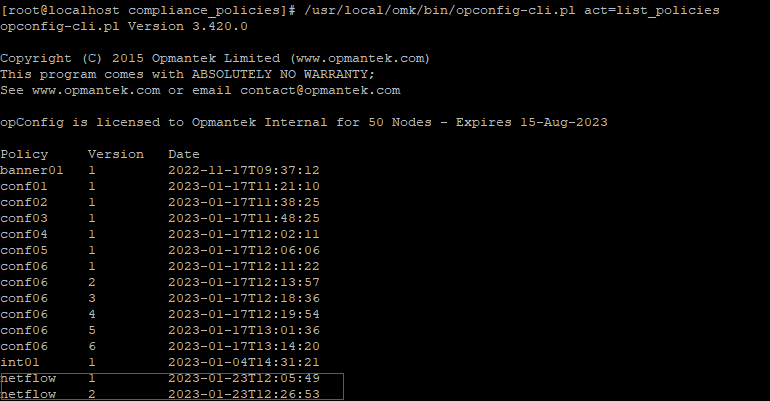
# /usr/local/omk/bin/opconfig-cli.pl act=list_policies |
| Info |
|---|
Always that you change the compliance policy file you must import the policy in order to update it. You will have a new version. |
At this time compliance policy assessments are not performed automatically but have to be triggered with opconfig-cli.pl:
We have to execute this command "/usr/local/omk/bin/opconfig-cli.pl act=check_compliance"
| Code Block |
|---|
# /usr/local/omk/bin/opconfig-cli.pl act=check_compliance name='netflow' node=FortinetTest debug=9 |
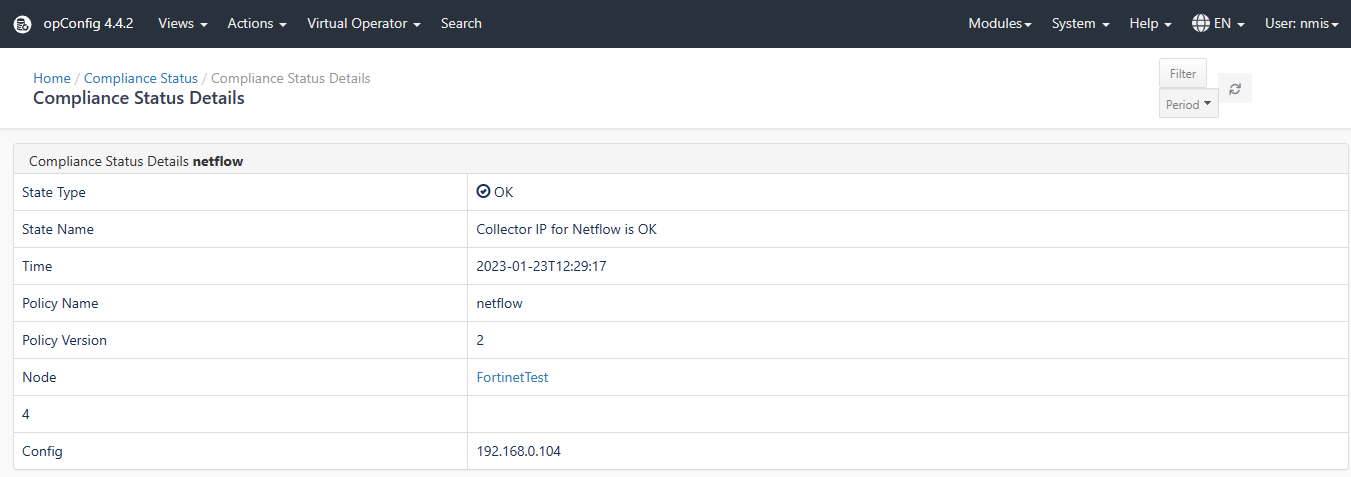
Step 3. View Compliance Status
Now you can check the Complaince Status in the opConfig GUI. Access the opConfig GUI at http://YOUR_SERVERNAME/omk/opConfig, login and then from the Menu Bar "Views -> Compliance Status".