Purpose
Demonstrate opFlowSP Role Based Access Control (RBAC) feature.
Feature Description
Service providers may want to allow customers to view flow statistics related to their interfaces, yet prevent them from viewing other customer interfaces. This feature facilitates this functionality.
Order of Operation
- Create a role (GUI)
- Create a user and assign a role (GUI)
- Create an object with a privilege tag (CLI)
- Associate the privilege tag with a role (CLI)
Configuration
Create a Role
From the opFlowSP main page, top menu bar, select System -> Portal Roles. This should render the following page.
Click the blue '+' button to add a role. At a minimum enter a name and click 'Add'.
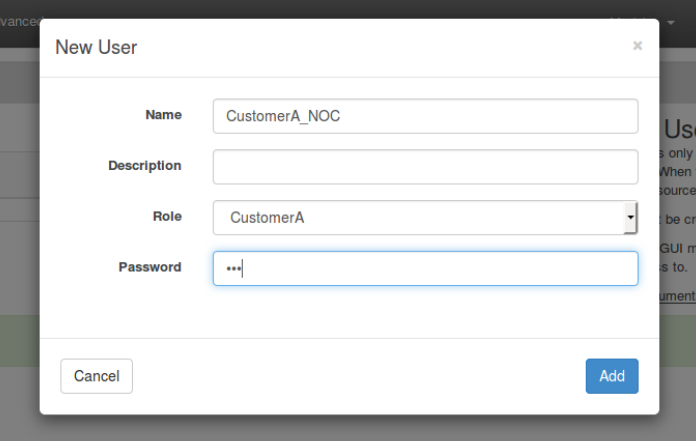
Create a User
From the opFlowSP top menu bar, select System -> Portal Users. This should render the following page.
Click the blue '+' button to an a user.
At a minimum do the following.
- Add a username
- From the Role drop down menu, choose a previously provisioned Role.
- Enter a password
Create an Object with a Privilege Tag
This is accomplished via the CLI. Objects are assigned a 'Privilege Tag'. These tags are latter associated with Roles; thus enabling users assigned to that Role to view them. The 'Privilege Tag' provides a lot of granularity.
The object in this example is a specific interface on a network device.
root@spflow:~# /usr/local/omk/bin/oprbac_admin.exe act=create-object path=root,opflowsp,agent,10.10.1.1,interface,3 read_privileges=CustomerA_read created new object
Syntax
/usr/local/omk/bin/oprbac_admin.exe act=create-object path=root,opflowsp,agent,<IP Address>,interface,<SNMP IF Number> read_privileges=<Privilege Tag>
- IP Address: The IP address that the network device uses to source flow data.
- SNMP IF Number: This is the SNMP index number of the interface in question.
- Privilege Tag: This tag is user defined and will be assigned to a role.
It's possible to set a privilege tag for an entire node by simply not adding the interface information. This would allow all the interfaces for a particular node to be viewed; for example:
/usr/local/omk/bin/oprbac_admin.exe act=create-object path=root,opflowsp,agent,<IP Address> read_privileges=<Privilege Tag>
Associate a Privilege Tag with a Role
This step is also accomplished via the CLI.
root@spflow:~# /usr/local/omk/bin/oprbac_admin.exe act=update-role name=CustomerA privileges=CustomerA_read updated role.
Syntax
/usr/local/omk/bin/oprbac_admin.exe act=update-role name=<Role Name> privileges=<Privilege Tag>
- Role Name: The role that the user is assigned to.
- Privilege Tag: The privilege tag that is associated with the previously defined interface object that the user is allowed to view.
Verification
Log in as the newly configured user and verify only the allowed interfaces are available.
The CLI can also be used to verify access as seen below.
root@spflow:~# /usr/local/omk/bin/oprbac_admin.exe act=list-users verbose=1 Name Description Roles Properties Privileges CustomerA_NOC CustomerA root@spflow:~# /usr/local/omk/bin/oprbac_admin.exe act=list-roles verbose=1 Name Description Properties Privileges CustomerA CustomerA_read root@spflow:~# /usr/local/omk/bin/oprbac_admin.exe act=list-objects verbose=1 Path Description Create Read Update Delete root,opflowsp,agent,10.10.1.1,interface,3 N/A CustomerA_read N/A N/A