| Table of Contents |
|---|
General User Authentication Information
For a simple set of configuration items for ALL types of User Authentication systems please refer here:
Setting up MS-LDAP authentication
Outline of the configuration items
'auth_ldap_context' => 'ou=people,dc = example, dc = com',# LDAP context to link. 'auth_method_1' => 'ms-ldap', #First type of Authentication can be followed by other types 'auth_ms_ldap_attr' => 'sAMAccountName',# the attribute that matches the username. 'auth_ms_ldap_base' => 'dc=corp, dc=example,dc=com',#base to search in LDAP 'auth_ms_ldap_dn_acc' => 'CN=omklatam, ou = Services, dc = OPMANTEK, dc = corp', # 'auth_ms_ldap_dn_psw' => 'password,', 'auth_ms_ldap_server' => 'host_LDAP: 389', |
Aspects to consider:
| Info | ||
|---|---|---|
| ||
To use SSL/TLS secured MS-LDAP (MS-LDAPS) see the differences in the table in User Management in NMIS8 . In summary it requires Optional Perl Modules: IO::Socket::SSL and Net::LDAPS and uses config items: If you use an internal CA for your AD LDAP SSL certificates you will need to import your internal root CA public certificates so that SSL can trust the connection. Search processes for your NMIS servers OS. |
LDAP Base: The base is the root of the Active Directory, since it is the place where the search of the users who need to authenticate will be carried out.Taking as reference the structure of the Active Directory will be as follows:
'auth_ms_ldap_base' => 'dc = OPMANTEK, dc = corp',#base to search in LDAP 'auth_ldap_context' => 'dc = OPMANTEK, dc = corp',# LDAP context |
The account is the service account which user is going to authenticate with the active directory, to enable the search of the LDAP Database for users.
Therefore, the first part is added is the service account username CN=omklatam
The second part is the OU = Servicescontainer.
The third part is the domain DC = OPMANTEK and DC = corp.
The result would be the following:
'auth_ms_ldap_dn_acc' => 'CN = omklatam, ou = Services, dc = OPMANTEK, dc = corp', |
Installation and configuration
.
- Make sureNet ::
...
- LDAP is up to date (
...
- minimum version 0.64).
[root @ opmantek] #cpan Net :: LDAP |
|---|
- Make
...
- sure that IO :: Socket :: SSLis new enough (must be
...
- 1998 or newer).
[root @ opmantek] #cpan -f IO :: Socket :: SSL |
|---|
...
Note:-
...
f is because some tests
...
do not pass on some
...
Copy CA cert onto server, in this example it goes into /tmp/YOUR_CACERT.pem, only pem files have been tested, others may work.
...
Add CA cert into DB (line requires a nickname, as well as the path to the cert copied onto the server)
| Code Block |
|---|
certutil -d /etc/openldap/certs/ -A -n YOUR_CERT_NICKNAME -i /tmp/YOUR_CACERT.pem -t "TCu,TCu,TCu" |
...
Verify the cert is in the DB
| Code Block |
|---|
[root@opmantek certs]# certutil -d /etc/openldap/certs/ -L
Certificate Nickname Trust Attributes
SSL,S/MIME,JAR/XPI
YOUR_CERT_NICKNAME CT,C,C |
machines.
- Configuration items as above in /usr/local/nmis8/conf/Config.nmis
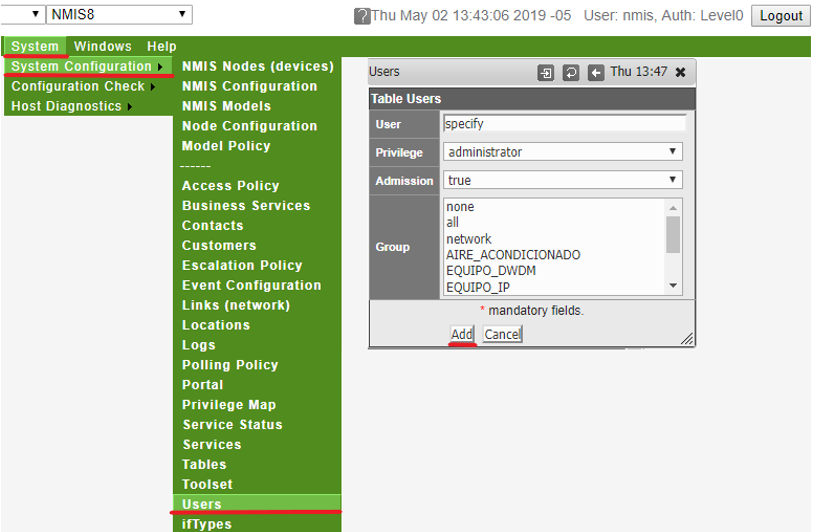
- Perform procedure to add users through the GUI or through the conf/Users.nmios file, the User field for each user must match the User's "sAMAccountName" attribute in AD. The Privilege should be set the appropriate Authorisation level.
- See here for more information on NMIS User authorisation User Management in NMIS8#AuthorisationinNMIS
- Try to access the credentials granted by the client in the NMIS portal.
Testing LDAP access
- Perform the installation of the following packages for troubleshooting.
[root @ opmantek] #yum -y install openldap-clients nss-pam-ldapd |
|---|
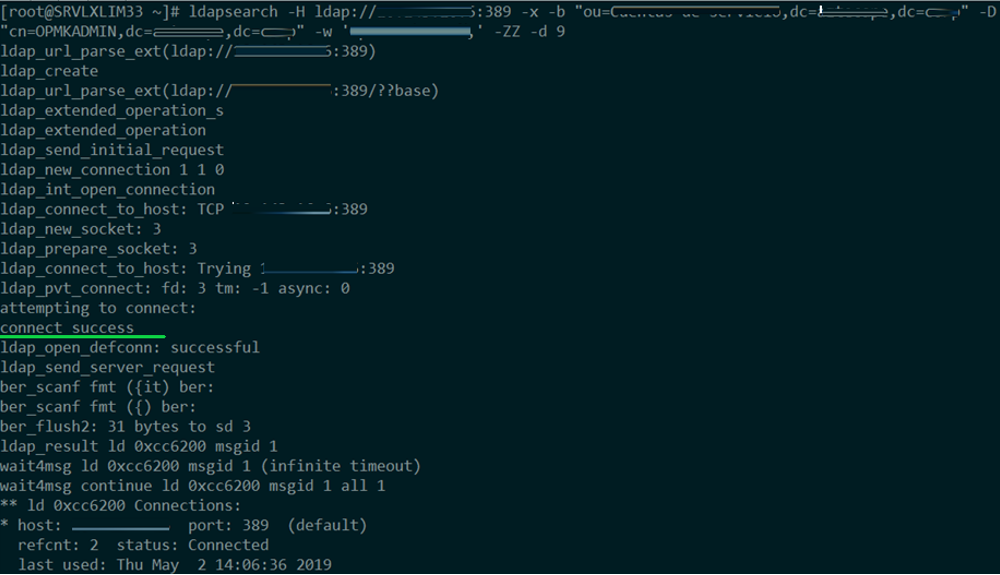
- Verify LDAP connectivity using ldapsearch, you will have to configure -H, -by
...
- -D, they can come from your current NMIS ms-ldap
...
- configuration if you have
...
- a:
...
- -b
...
- is auth_ms_ldap_base, -D
...
- isauth_ms_ldap_dn_acc
...
...
ldapsearch |
|---|
...
-H |
|---|
...
ldap: // |
|---|
...
ip_LDAP: 389 |
|---|
...
-x |
|---|
...
-b |
|---|
...
" |
|---|
...
ou = |
|---|
...
User container, dc = |
|---|
...
domain, dc = |
|---|
...
domain" |
|---|
...
-D |
|---|
...
"cn = |
|---|
...
user_ldap, dc = |
|---|
...
domain, dc = |
|---|
...
domain" |
|---|
...
-w |
|---|
...
'password_user' |
|---|
...
- ZZ |
|---|
...
-d |
|---|
...
Change NMIS Auth code to use certificate directory, note it's using LDAP instead of LDAPS and adds a new line with a new config item.
| Code Block |
|---|
# /usr/local/nmis8/lib/Auth.pm (line 716 approx)
# change
$ldap = new Net::LDAPS($C->{'auth_ms_ldaps_server'});
# to
$ldap = new Net::LDAP($C->{'auth_ms_ldaps_server'}, version => 3);
my $mesg = $ldap->start_tls( capath => $C->{'auth_openldap_certs'} ); |
...
Modify configuration to use ms-ldaps and set new auth_openldap_certs path
| Code Block |
|---|
'auth_method_1' => 'ms-ldaps',
'auth_ms_ldaps_server' => 'ad-server.name.or.ip',
'auth_openldap_certs' => '/etc/openldap/certs/', # this line is new
'auth_ms_ldap_attr' => 'sAMAccountName',
'auth_ms_ldap_base' => 'DC=corp,DC=shurely,DC=com,DC=nz'
'auth_ms_ldap_dn_acc' => 'LDAPRead',
'auth_ms_ldap_dn_psw' => 'SecurePassword123', |
...
9 |
|---|
Note: Possibly it shows an SSL certificate error, this error is irrelevant since although the connection is shown it has been successful.
MS-LDAPS (secure LDAP with SSL/TLS) - how to trust your internal CA root certificate
Users.nmis will need to have an entry for each user who can authenticate or the default settings for a user will need to be set.
...