Overview
Open-AudIT can take the supplied username and password in the web login form and verify these against Active Directory to allow login.
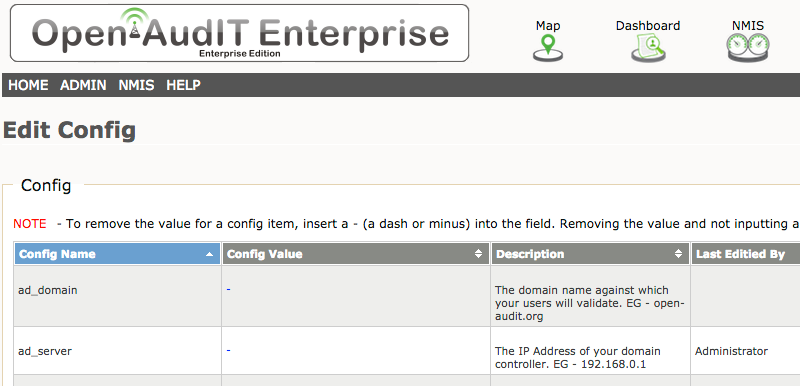
To configure this, go to Menu -> Admin -> Config and set the fields ad_domain and ad_server.
ad_domain - This is the Windows Active Directory domain name that your users will validate against. For example open-audit.com.
ad_server - This is the ip address of the actual Active Directory server you would like to use for user validation.
Your user should already have a logon to Open-AudIT with a password and any required Group privileges assigned.
When the user inputs their logon details, if the above (ad_domain, ad_server) fields are populated, Open-AudIT will ask Active Directory if the credentials are correct and if so, allow the user to log on.
The reason for setting a local user password in addition (inside Open-AudIT) is so that if Active Directory validation is not working (if the domain controller is offline or some other issue), Open-AudIT will attempt to validate via Active Directory but if this fails will validate the credentials against the internal Open-AudIT credentials and if they match will still allow logon. You can still logon even if Active Directory is not available
Being configured in this way also enables you to have AD using Active Directory for logon, but also enables you to create Open-AudIT users with no Active Directory account.
use Active Directory and/or OpenLDAP for user authentication and authorisation.
How To
To enable this, create a new LDAP Server item by going to menu -> Manage -> LDAP Servers -> Create LDAP Servers.
Input the relevant details for either Active Directory or OpenLDAP.
Once you have done this, Open-AudIT will attempt to verify your user logon details against an LDAP server. If the user has valid LDAP credentials, Open-AudIT will ask LDAP for the list of groups (in LDAP) that the user is in. If the user is in the corresponding groups for Open-AudIT Roles and Orgs, those Roles and Orgs will be applied to that user.
If the user account does not actually exist within Open-AudIT, it will be created. If it does exist, the details such as email, full name, etc will be updated.
If the user either doesn't have valid LDAP credentials or is not in at least one Open-AudIT Role and Group, Open-AudIT will fallback to using local Open-AudIT user details and attempt authentication and authorization there. Failing that, the user will be denied access.
The user in LDAP must be a direct member of the required Open-AudIT groups for Roles and Orgs. A member of a group that is a member another group that is a member of the Open-AudIT group will not work (at this stage).
If a new Org is created, an LDAP group name is automatically derived from the name. For example, if a new Org is created and is named Test, the corresponding LDAP group will be named open-audit_orgs_test.
Roles can only be created and edited if you have an Open-AudIT Enterprise license. For most users, the default set of Roles should be all that is required. And if you think about it, it's more granularity than Open-AudIT has ever had at any time!
That's all there is to it. As long as Open-AudIT can talk to an LDAP Server - be it an Active Directory Domain Controller or an OpenLDAP server, your users can use their existing Active Directory LDAP credentials to logon to Open-AudIT.
The default Open-AudIT groups for LDAP Server authorization are:
Roles Groups
| Code Block |
|---|
+-----------+----------------------------+
| name | ad_group |
+-----------+----------------------------+
| admin | open-audit_roles_admin |
| org_admin | open-audit_roles_org_admin |
| reporter | open-audit_roles_reporter |
| user | open-audit_roles_user |
+-----------+----------------------------+ |
Orgs Groups
| Code Block |
|---|
+----------------------+--------------------------------------+
| name | ad_group |
+----------------------+--------------------------------------+
| Default Organisation | open-audit_orgs_default_organisation |
+----------------------+--------------------------------------+ |