Introduction
NMIS 8.4G introduced general availability of the full authorisation and authentication model in NMIS using internal or external authentication methods. This ensures that NMIS remains an enterprise class network management system. Once authenticated a user is looked up in the internal authorisation system to determine their role, this role is customisable and extensible.
The implementation of the authorisation, limits groups of users by roles to specific things they can view and do with NMIS, and groups of devices/nodes on which they can do it. This is commonly referred to as role based access control.
Authentication Methods
The following table lists the NMIS configuration option and the type of authentication which it works with.
| Method | Description |
|---|---|
| apache | Apache will perform authentication and provide an authenticated user to NMIS, which will have authorisation policies applied. |
| htpasswd | NMIS will use the users defined in the NMIS Users file, by default /usr/local/nmis8/conf/users.dat |
| ldap and ldaps | NMIS will use the configured LDAP server to perform authentication |
ms-ldap and ms-ldaps | NMIS will use the configured Microsoft Active Directory (LDAP) server to perform authentication |
| radius | NMIS will use the configured radius server (Cisco ACS or Steel Belted Radius for example) |
| tacacs | NMIS will use the configured Tacacs+ server (Cisco ACS for example) |
Configuration of the External Authentications
In the NMIS configuration you can configure multiple methods which are used for auth failure, so if ms-ldap fails, it will fail back to htpasswd for example. This means if you set auth_method_1 to be ldap and auth_method_2 to be htpasswd, and login with the default NMIS credentials (and you have not changed the password), the authentication for LDAP will fail, and then authentication with the users.dat will succeed and the user will be logged in.
It is important to change your default passwords if you expect any level of security.
Default Privilege Level for Authenticated Users
When accessing NMIS, you have a choice on how to handle authenticated users who do not have authorisations defined, you can reject them, or you can allow them default access.
This is so that you do not have to define every user in the system if the authentication system is providing a reduced list of users, to have the users become an operator or guest by default and be able to see all groups of devices, the following would apply.
'auth_default_privilege' => 'guest',
'auth_default_groups' => 'all',
To prevent default authorisation, simply define them as blank, which is the default in the NMIS8 Install configuration.
NMIS Single Sign On
Configuring Single Sign On
At great expense to Opmantek NMIS now includes a single sign on (SSO) feature, this requires cookies to work. To enable the feature, all that is required is to use a fully qualified domain name (FQDN) for your NMIS server, e.g. nmis1.domain.com and then in the NMIS configuration of all NMIS servers participating, configure the auth_sso_domain and auth_web_key in /usr/local/nmis8/conf/Config.nmis, the default is set to ".domain.com", e.g.
'auth_sso_domain' => '.domain.com', 'auth_web_key' => 'thisismysecretkey',
Two periods are required in the domain name are required, so if your company is AJAX Cleaning and your domain name is ajaxcleaning.com this configuration would be:
'auth_sso_domain' => '.ajaxcleaning.com',
Accessing NMIS for Single Sign On
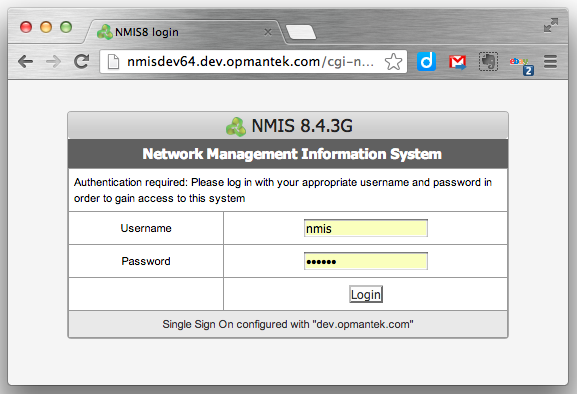
When you are accessing the NMIS server after this is configured you must then use the FQDN, in our development labs we use dev.opmantek.com which contains two periods, so we can configure it like so:
'auth_sso_domain' => 'dev.opmantek.com',
Then when we browse to the servers, we use the full name of the server, e.g. nmisdev64.dev.opmantek.com and the login banner tells us that Single Sign On is configured with "dev.opmantek.com", I can enter the password and access the server.
If I were to use the IP address to access the server, authentication will succeed but the cookie will not be created correctly and you will be logged out again.
When NMIS Single Sign On is configured you MUST use the Full Qualified Domain Name to access the server.
Adding a New User to NMIS8 with htpasswd Method
To add a new user to NMIS8 while it is using Apache for Authentication and assuming that Apache has not already been integrated with LDAP, Active Directory, Radius, or the like, you will need to create a new Web Based user, this is done with the following commands (assuming that nmis8 is installed in the default location):
cd /usr/local/nmis8/conf
htpasswd -d users.dat <new user>
<enter password when prompted>
This adds the user for Authentication, now the application needs to be able to Authorise the user.
Login to the NMIS Portal, as an administration user, the normal URL is http://nmisserver/cgi-nmis8/nmiscgi.pl
Using the menu access "System -> System Configuration -> Users", select "add" from the top right, and then complete the form, specifying the User which matches the user added using htpasswd, specify Privilege and Groups, using "all" if all groups are permitted, multiple groups can be selected.
Default Encryption and htpasswd
Apache documentation suggests that the default encryption for htpasswd is MD5, but testing done by NMIS development team shows it is crypt compatible, if you are having problems with this, you can test yourself.
htpasswd -b -c users.default.dat nmis nm1888 htpasswd -b -d -c users.crypt.dat nmis nm1888 htpasswd -b -m -c users.md5.dat nmis nm1888 # Make sure NMIS is using 'auth_htpasswd_encrypt' => 'crypt', cp users.default.dat users.dat # Logout login -> Success cp users.crypt.dat users.dat # Logout, login -> Success # Make sure Perl module "Digest::MD5" is installed # Make sure NMIS is using 'auth_htpasswd_encrypt' => 'md5', # Logout, login, -> FAIL cp users.md5.dat users.dat # Logout, login, -> Success (this failed for me, I could not get MD5 to work.)
User Case
User names in many systems are not case sensitive, so NMIS will handle usernames in lower case, when adding users to Users.nmis, ensure that the name is all in LOWER CASE.
Spaces in User Names
At great expense to Opmantek, support for usernames with spaces has been added, this is in the next release to be numbered 8.3.14G or higher.